QEMU/KVM/libvirtをRocky Linux 8.7にインストール
Rocky Linux 8.7での例、AlmaLinux 8.7でも同様。
パッケージのインストール
必須パッケージ
dnf install qemu-kvm libvirt systemctl start libvirtd
CUI用のツール
dnf install virt-install virt-top virt-dib virt-v2v libguestfs-tools libguestfs-bash-completion libguestfs-rsync perl-XML-XPath
GUI用のツール
yum install virt-manager virt-viewer
インストールするパッケージの概要
| パッケージ名 | 主要なコマンド | 概要 | |
|---|---|---|---|
| qemu-kvm | qemu-kvm 6.2.0 | 必須 | |
| qemu-img | qemu-img | 仮想ディスクイメージの操作 | |
| libvirt | libvirt 8.0.0 | 必須 | |
| libvirt-client | virsh, virt-host-validate, libvirt-guests.service | 基本ツール | |
| virt-install | virt-install | 仮想マシンの作成 | |
| virt-top | virt-top | ||
| virt-dib | virt-dib | 仮想ディスクイメージの作成 | |
| virt-v2v | virt-v2v | 仮想マシンの変換 | |
| libguestfs-tools | guestfish, virt-sysprep, virt-df, virt-ls | ゲスト(の中のファイル)を操作するツール | |
| libguestfs | libguestfs 1.40.2 | ||
| libguestfs-xfs | XFSのディスクイメージ操作 | ||
| libguestfs-rsync | ディスクイメージをrsyncで操作 | ||
| perl-XML-XPath | xpath | ||
仮想化環境の設定
virt-host-validate
全てPASS、あるいはWARNであること。
IOMMUの有効化
QEMU: Checking if IOMMU is enabled by kernel : WARN (IOMMU appears to be disabled in kernel. Add intel_iommu=on to kernel cmdline arguments)と表示された場合。
vi /etc/sysconfig/grub
CPUがIntel製ならGRUB_CMDLINE_LINUXにintel_iommu=on iommu=ptを追加。
AMD製ならiommu=ptを追加。
grub2-mkconfig -o /etc/grub2.cfg reboot
Secure Guest supportについての警告
QEMU: Checking for secure guest support : WARN (Unknown if this platform has Secure Guest support)と表示された場合。
IntelのCPUなら無視。
https://github.com/libvirt/libvirt/blob/v8.0.0/src/qemu/qemu_capabilities.c#L4780
/sys/module/kvm_amd/parameters/sevの値と/dev/sevの存在をチェックしているようで、
AMD Secure Encrypted VirtualizationをサポートしているCPUでのみ有効になる。
サポートOSの一覧
virt-installの--os-variantに設定可能な値。
osinfo-query os
一部抜粋
| Short ID | Name |
|---|---|
| almalinux8 | AlmaLinux 8 |
| almalinux9 | AlmaLinux 9 |
| centos7.0 | CentOS 7 |
| centos8 | CentOS 8 |
| debian10 | Debian 10 |
| debian11 | Debian 11 |
| freebsd12.3 | FreeBSD 12.3 |
| freebsd13.1 | FreeBSD 13.1 |
| rhel7.9 | Red Hat Enterprise Linux 7.9 |
| rhel8-unknown | Red Hat Enterprise Linux 8 Unknown |
| rhel8.7 | Red Hat Enterprise Linux 8.7 |
| rhel9-unknown | Red Hat Enterprise Linux 9 Unknown |
| rhel9.1 | Red Hat Enterprise Linux 9.1 |
| rocky8-unknown | Rocky Linux 8 Unknown |
| rocky8.6 | Rocky Linux 8.6 |
| rocky9-unknown | Rocky Linux 9 Unknown |
| rocky9.0 | Rocky Linux 9.0 |
libvirtが作成するデフォルトNATネットワークの設定内容
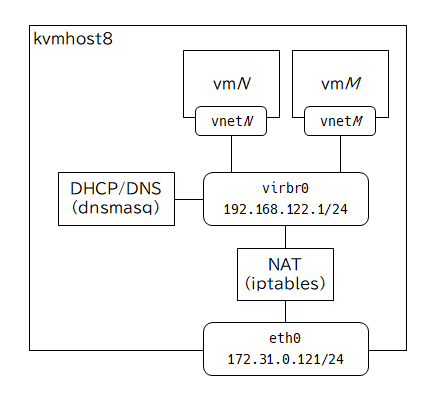
[root@kvmhost8 ~]# virsh net-dumpxml default
<network>
<name>default</name>
<uuid>64d043de-0618-4c40-bfc0-22f7c095c601</uuid>
<forward mode='nat'>
<nat>
<port start='1024' end='65535'/>
</nat>
</forward>
<bridge name='virbr0' stp='on' delay='0'/>
<mac address='52:54:00:4d:37:44'/>
<ip address='192.168.122.1' netmask='255.255.255.0'>
<dhcp>
<range start='192.168.122.2' end='192.168.122.254'/>
</dhcp>
</ip>
</network>
[root@kvmhost8 ~]# nmcli con
NAME UUID TYPE DEVICE
eth0 d2413e87-5b95-4ada-b395-6c216165adfd ethernet eth0
virbr0 a5dd396b-4e89-4f5b-92ab-c5c7fbfc6c65 bridge virbr0
[root@kvmhost8 ~]# nmcli dev
DEVICE TYPE STATE CONNECTION
eth0 ethernet connected eth0
virbr0 bridge connected (externally) virbr0
lo loopback unmanaged --
[root@kvmhost8 ~]# nmcli -f connection.zone con show eth0
connection.zone: --
[root@kvmhost8 ~]# nmcli -f connection.zone con show virbr0
connection.zone: --
[root@kvmhost8 ~]# nmcli dev show virbr0
GENERAL.DEVICE: virbr0
GENERAL.TYPE: bridge
GENERAL.HWADDR: 52:54:00:4D:37:44
GENERAL.MTU: 1500
GENERAL.STATE: 100 (connected (externally))
GENERAL.CONNECTION: virbr0
GENERAL.CON-PATH: /org/freedesktop/NetworkManager/ActiveConnection/2
IP4.ADDRESS[1]: 192.168.122.1/24
IP4.GATEWAY: --
IP4.ROUTE[1]: dst = 192.168.122.0/24, nh = 0.0.0.0, mt = 0
IP6.GATEWAY: --
[root@kvmhost8 ~]# ip netns
[root@kvmhost8 ~]# ip -detail link
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 promiscuity 0 minmtu 0 maxmtu 0 addrgenmode eui64 numtxqueues 1 numrxqueues 1 gso_max_size 65536 gso_max_segs 65535
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000
link/ether 00:15:5d:00:24:30 brd ff:ff:ff:ff:ff:ff promiscuity 0 minmtu 68 maxmtu 65521 addrgenmode none numtxqueues 64 numrxqueues 64 gso_max_size 62780 gso_max_segs 65535
3: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN mode DEFAULT group default qlen 1000
link/ether 52:54:00:4d:37:44 brd ff:ff:ff:ff:ff:ff promiscuity 0 minmtu 68 maxmtu 65535
bridge forward_delay 200 hello_time 200 max_age 2000 ageing_time 30000 stp_state 1 priority 32768 vlan_filtering 0 vlan_protocol 802.1Q bridge_id 8000.52:54:0:4d:37:44 designated_root 8000.52:54:0:4d:37:44 root_port 0 root_path_cost 0 topology_change 0 topology_change_detected 0 hello_timer 0.82 tcn_timer 0.00 topology_change_timer 0.00 gc_timer 2.81 vlan_default_pvid 1 vlan_stats_enabled 0 vlan_stats_per_port 0 group_fwd_mask 0 group_address 01:80:c2:00:00:00 mcast_snooping 1 mcast_router 1 mcast_query_use_ifaddr 0 mcast_querier 0 mcast_hash_elasticity 16 mcast_hash_max 4096 mcast_last_member_count 2 mcast_startup_query_count 2 mcast_last_member_interval 100 mcast_membership_interval 26000 mcast_querier_interval 25500 mcast_query_interval 12500 mcast_query_response_interval 1000 mcast_startup_query_interval 3125 mcast_stats_enabled 0 mcast_igmp_version 2 mcast_mld_version 1 nf_call_iptables 0 nf_call_ip6tables 0 nf_call_arptables 0 addrgenmode eui64 numtxqueues 1 numrxqueues 1 gso_max_size 65536 gso_max_segs 65535
[root@kvmhost8 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:15:5d:00:24:30 brd ff:ff:ff:ff:ff:ff
inet 172.31.0.121/24 brd 172.31.0.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::215:5dff:fe00:2430/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 52:54:00:4d:37:44 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
[root@kvmhost8 ~]# ip route
default via 172.31.0.1 dev eth0 proto static metric 100
172.31.0.0/24 dev eth0 proto kernel scope link src 172.31.0.121 metric 100
192.168.122.0/24 dev virbr0 proto kernel scope link src 192.168.122.1 linkdown
[root@kvmhost8 ~]# ps ax | grep [d]nsmasq 1328 ? S 0:00 /usr/sbin/dnsmasq --conf-file=/var/lib/libvirt/dnsmasq/default.conf --leasefile-ro --dhcp-script=/usr/libexec/libvirt_leaseshelper 1329 ? S 0:00 /usr/sbin/dnsmasq --conf-file=/var/lib/libvirt/dnsmasq/default.conf --leasefile-ro --dhcp-script=/usr/libexec/libvirt_leaseshelper [root@kvmhost8 ~]# cat /var/lib/libvirt/dnsmasq/default.conf ##WARNING: THIS IS AN AUTO-GENERATED FILE. CHANGES TO IT ARE LIKELY TO BE ##OVERWRITTEN AND LOST. Changes to this configuration should be made using: ## virsh net-edit default ## or other application using the libvirt API. ## ## dnsmasq conf file created by libvirt strict-order pid-file=/run/libvirt/network/default.pid except-interface=lo bind-dynamic interface=virbr0 dhcp-range=192.168.122.2,192.168.122.254,255.255.255.0 dhcp-no-override dhcp-authoritative dhcp-lease-max=253 dhcp-hostsfile=/var/lib/libvirt/dnsmasq/default.hostsfile addn-hosts=/var/lib/libvirt/dnsmasq/default.addnhosts [root@kvmhost8 ~]# cat /var/lib/libvirt/dnsmasq/default.hostsfile [root@kvmhost8 ~]# cat /var/lib/libvirt/dnsmasq/default.addnhosts
[root@kvmhost8 ~]# cat /proc/sys/net/ipv4/ip_forward 1 [root@kvmhost8 ~]# iptables -S -t filter -P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT -N LIBVIRT_INP -N LIBVIRT_OUT -N LIBVIRT_FWO -N LIBVIRT_FWI -N LIBVIRT_FWX -A INPUT -j LIBVIRT_INP -A FORWARD -j LIBVIRT_FWX -A FORWARD -j LIBVIRT_FWI -A FORWARD -j LIBVIRT_FWO -A OUTPUT -j LIBVIRT_OUT -A LIBVIRT_INP -i virbr0 -p udp -m udp --dport 53 -j ACCEPT -A LIBVIRT_INP -i virbr0 -p tcp -m tcp --dport 53 -j ACCEPT -A LIBVIRT_INP -i virbr0 -p udp -m udp --dport 67 -j ACCEPT -A LIBVIRT_INP -i virbr0 -p tcp -m tcp --dport 67 -j ACCEPT -A LIBVIRT_OUT -o virbr0 -p udp -m udp --dport 53 -j ACCEPT -A LIBVIRT_OUT -o virbr0 -p tcp -m tcp --dport 53 -j ACCEPT -A LIBVIRT_OUT -o virbr0 -p udp -m udp --dport 68 -j ACCEPT -A LIBVIRT_OUT -o virbr0 -p tcp -m tcp --dport 68 -j ACCEPT -A LIBVIRT_FWO -s 192.168.122.0/24 -i virbr0 -j ACCEPT -A LIBVIRT_FWO -i virbr0 -j REJECT --reject-with icmp-port-unreachable -A LIBVIRT_FWI -d 192.168.122.0/24 -o virbr0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A LIBVIRT_FWI -o virbr0 -j REJECT --reject-with icmp-port-unreachable -A LIBVIRT_FWX -i virbr0 -o virbr0 -j ACCEPT [root@kvmhost8 ~]# iptables -S -t nat -P PREROUTING ACCEPT -P INPUT ACCEPT -P POSTROUTING ACCEPT -P OUTPUT ACCEPT -N LIBVIRT_PRT -A POSTROUTING -j LIBVIRT_PRT -A LIBVIRT_PRT -s 192.168.122.0/24 -d 224.0.0.0/24 -j RETURN -A LIBVIRT_PRT -s 192.168.122.0/24 -d 255.255.255.255/32 -j RETURN -A LIBVIRT_PRT -s 192.168.122.0/24 ! -d 192.168.122.0/24 -p tcp -j MASQUERADE --to-ports 1024-65535 -A LIBVIRT_PRT -s 192.168.122.0/24 ! -d 192.168.122.0/24 -p udp -j MASQUERADE --to-ports 1024-65535 -A LIBVIRT_PRT -s 192.168.122.0/24 ! -d 192.168.122.0/24 -j MASQUERADE [root@kvmhost8 ~]# iptables -S -t mangle -P PREROUTING ACCEPT -P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT -P POSTROUTING ACCEPT -N LIBVIRT_PRT -A POSTROUTING -j LIBVIRT_PRT -A LIBVIRT_PRT -o virbr0 -p udp -m udp --dport 68 -j CHECKSUM --checksum-fill [root@kvmhost8 ~]# iptables -S -t raw -P PREROUTING ACCEPT -P OUTPUT ACCEPT [root@kvmhost8 ~]# iptables -S -t security -P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT
[root@kvmhost8 ~]# nft -s list ruleset
table ip filter {
chain INPUT {
type filter hook input priority filter; policy accept;
counter jump LIBVIRT_INP
}
chain FORWARD {
type filter hook forward priority filter; policy accept;
counter jump LIBVIRT_FWX
counter jump LIBVIRT_FWI
counter jump LIBVIRT_FWO
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
counter jump LIBVIRT_OUT
}
chain LIBVIRT_INP {
iifname "virbr0" meta l4proto udp udp dport 53 counter accept
iifname "virbr0" meta l4proto tcp tcp dport 53 counter accept
iifname "virbr0" meta l4proto udp udp dport 67 counter accept
iifname "virbr0" meta l4proto tcp tcp dport 67 counter accept
}
chain LIBVIRT_OUT {
oifname "virbr0" meta l4proto udp udp dport 53 counter accept
oifname "virbr0" meta l4proto tcp tcp dport 53 counter accept
oifname "virbr0" meta l4proto udp udp dport 68 counter accept
oifname "virbr0" meta l4proto tcp tcp dport 68 counter accept
}
chain LIBVIRT_FWO {
iifname "virbr0" ip saddr 192.168.122.0/24 counter accept
iifname "virbr0" counter reject
}
chain LIBVIRT_FWI {
oifname "virbr0" ip daddr 192.168.122.0/24 ct state related,established counter accept
oifname "virbr0" counter reject
}
chain LIBVIRT_FWX {
iifname "virbr0" oifname "virbr0" counter accept
}
}
table ip6 filter {
chain INPUT {
type filter hook input priority filter; policy accept;
counter jump LIBVIRT_INP
}
chain FORWARD {
type filter hook forward priority filter; policy accept;
counter jump LIBVIRT_FWX
counter jump LIBVIRT_FWI
counter jump LIBVIRT_FWO
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
counter jump LIBVIRT_OUT
}
chain LIBVIRT_INP {
}
chain LIBVIRT_OUT {
}
chain LIBVIRT_FWO {
}
chain LIBVIRT_FWI {
}
chain LIBVIRT_FWX {
}
}
table bridge filter {
chain INPUT {
type filter hook input priority filter; policy accept;
}
chain FORWARD {
type filter hook forward priority filter; policy accept;
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
}
}
table ip security {
chain INPUT {
type filter hook input priority 150; policy accept;
}
chain FORWARD {
type filter hook forward priority 150; policy accept;
}
chain OUTPUT {
type filter hook output priority 150; policy accept;
}
}
table ip raw {
chain PREROUTING {
type filter hook prerouting priority raw; policy accept;
}
chain OUTPUT {
type filter hook output priority raw; policy accept;
}
}
table ip mangle {
chain PREROUTING {
type filter hook prerouting priority mangle; policy accept;
}
chain INPUT {
type filter hook input priority mangle; policy accept;
}
chain FORWARD {
type filter hook forward priority mangle; policy accept;
}
chain OUTPUT {
type route hook output priority mangle; policy accept;
}
chain POSTROUTING {
type filter hook postrouting priority mangle; policy accept;
counter jump LIBVIRT_PRT
}
chain LIBVIRT_PRT {
oifname "virbr0" meta l4proto udp udp dport 68 counter # CHECKSUM fill
}
}
table ip nat {
chain PREROUTING {
type nat hook prerouting priority dstnat; policy accept;
}
chain INPUT {
type nat hook input priority 100; policy accept;
}
chain POSTROUTING {
type nat hook postrouting priority srcnat; policy accept;
counter jump LIBVIRT_PRT
}
chain OUTPUT {
type nat hook output priority -100; policy accept;
}
chain LIBVIRT_PRT {
ip saddr 192.168.122.0/24 ip daddr 224.0.0.0/24 counter return
ip saddr 192.168.122.0/24 ip daddr 255.255.255.255 counter return
meta l4proto tcp ip saddr 192.168.122.0/24 ip daddr != 192.168.122.0/24 counter masquerade to :1024-65535
meta l4proto udp ip saddr 192.168.122.0/24 ip daddr != 192.168.122.0/24 counter masquerade to :1024-65535
ip saddr 192.168.122.0/24 ip daddr != 192.168.122.0/24 counter masquerade
}
}
table ip6 security {
chain INPUT {
type filter hook input priority 150; policy accept;
}
chain FORWARD {
type filter hook forward priority 150; policy accept;
}
chain OUTPUT {
type filter hook output priority 150; policy accept;
}
}
table ip6 raw {
chain PREROUTING {
type filter hook prerouting priority raw; policy accept;
}
chain OUTPUT {
type filter hook output priority raw; policy accept;
}
}
table ip6 mangle {
chain PREROUTING {
type filter hook prerouting priority mangle; policy accept;
}
chain INPUT {
type filter hook input priority mangle; policy accept;
}
chain FORWARD {
type filter hook forward priority mangle; policy accept;
}
chain OUTPUT {
type route hook output priority mangle; policy accept;
}
chain POSTROUTING {
type filter hook postrouting priority mangle; policy accept;
counter jump LIBVIRT_PRT
}
chain LIBVIRT_PRT {
}
}
table ip6 nat {
chain PREROUTING {
type nat hook prerouting priority dstnat; policy accept;
}
chain INPUT {
type nat hook input priority 100; policy accept;
}
chain POSTROUTING {
type nat hook postrouting priority srcnat; policy accept;
counter jump LIBVIRT_PRT
}
chain OUTPUT {
type nat hook output priority -100; policy accept;
}
chain LIBVIRT_PRT {
}
}
table bridge nat {
chain PREROUTING {
type filter hook prerouting priority dstnat; policy accept;
}
chain OUTPUT {
type filter hook output priority out; policy accept;
}
chain POSTROUTING {
type filter hook postrouting priority srcnat; policy accept;
}
}
table inet firewalld {
ct helper helper-tftp-udp {
type "tftp" protocol udp
l3proto inet
}
chain raw_PREROUTING {
type filter hook prerouting priority raw + 10; policy accept;
icmpv6 type { nd-router-advert, nd-neighbor-solicit } accept
meta nfproto ipv6 fib saddr . iif oif missing drop
}
chain mangle_PREROUTING {
type filter hook prerouting priority mangle + 10; policy accept;
jump mangle_PREROUTING_POLICIES_pre
jump mangle_PREROUTING_ZONES_SOURCE
jump mangle_PREROUTING_ZONES
jump mangle_PREROUTING_POLICIES_post
}
chain mangle_PREROUTING_POLICIES_pre {
jump mangle_PRE_policy_allow-host-ipv6
}
chain mangle_PREROUTING_ZONES_SOURCE {
}
chain mangle_PREROUTING_ZONES {
iifname "virbr0" goto mangle_PRE_libvirt
iifname "eth0" goto mangle_PRE_public
goto mangle_PRE_public
}
chain mangle_PREROUTING_POLICIES_post {
}
chain filter_INPUT {
type filter hook input priority filter + 10; policy accept;
ct state { established, related } accept
ct status dnat accept
iifname "lo" accept
jump filter_INPUT_POLICIES_pre
jump filter_INPUT_ZONES_SOURCE
jump filter_INPUT_ZONES
jump filter_INPUT_POLICIES_post
ct state { invalid } drop
reject with icmpx type admin-prohibited
}
chain filter_FORWARD {
type filter hook forward priority filter + 10; policy accept;
ct state { established, related } accept
ct status dnat accept
iifname "lo" accept
ip6 daddr { ::/96, ::ffff:0.0.0.0/96, 2002::/24, 2002:a00::/24, 2002:7f00::/24, 2002:a9fe::/32, 2002:ac10::/28, 2002:c0a8::/32, 2002:e000::/19 } reject with icmpv6 type addr-unreachable
jump filter_FORWARD_POLICIES_pre
jump filter_FORWARD_IN_ZONES_SOURCE
jump filter_FORWARD_IN_ZONES
jump filter_FORWARD_OUT_ZONES_SOURCE
jump filter_FORWARD_OUT_ZONES
jump filter_FORWARD_POLICIES_post
ct state { invalid } drop
reject with icmpx type admin-prohibited
}
chain filter_OUTPUT {
type filter hook output priority filter + 10; policy accept;
oifname "lo" accept
ip6 daddr { ::/96, ::ffff:0.0.0.0/96, 2002::/24, 2002:a00::/24, 2002:7f00::/24, 2002:a9fe::/32, 2002:ac10::/28, 2002:c0a8::/32, 2002:e000::/19 } reject with icmpv6 type addr-unreachable
jump filter_OUTPUT_POLICIES_pre
jump filter_OUTPUT_POLICIES_post
}
chain filter_INPUT_POLICIES_pre {
jump filter_IN_policy_allow-host-ipv6
}
chain filter_INPUT_ZONES_SOURCE {
}
chain filter_INPUT_ZONES {
iifname "virbr0" goto filter_IN_libvirt
iifname "eth0" goto filter_IN_public
goto filter_IN_public
}
chain filter_INPUT_POLICIES_post {
}
chain filter_FORWARD_POLICIES_pre {
}
chain filter_FORWARD_IN_ZONES_SOURCE {
}
chain filter_FORWARD_IN_ZONES {
iifname "virbr0" goto filter_FWDI_libvirt
iifname "eth0" goto filter_FWDI_public
goto filter_FWDI_public
}
chain filter_FORWARD_OUT_ZONES_SOURCE {
}
chain filter_FORWARD_OUT_ZONES {
oifname "virbr0" goto filter_FWDO_libvirt
oifname "eth0" goto filter_FWDO_public
goto filter_FWDO_public
}
chain filter_FORWARD_POLICIES_post {
}
chain filter_OUTPUT_POLICIES_pre {
}
chain filter_OUTPUT_POLICIES_post {
}
chain filter_IN_public {
jump filter_IN_public_pre
jump filter_IN_public_log
jump filter_IN_public_deny
jump filter_IN_public_allow
jump filter_IN_public_post
meta l4proto { icmp, ipv6-icmp } accept
}
chain filter_IN_public_pre {
}
chain filter_IN_public_log {
}
chain filter_IN_public_deny {
}
chain filter_IN_public_allow {
tcp dport 22 ct state { new, untracked } accept
ip6 daddr fe80::/64 udp dport 546 ct state { new, untracked } accept
tcp dport 9090 ct state { new, untracked } accept
}
chain filter_IN_public_post {
}
chain filter_FWDO_public {
jump filter_FWDO_public_pre
jump filter_FWDO_public_log
jump filter_FWDO_public_deny
jump filter_FWDO_public_allow
jump filter_FWDO_public_post
}
chain filter_FWDO_public_pre {
}
chain filter_FWDO_public_log {
}
chain filter_FWDO_public_deny {
}
chain filter_FWDO_public_allow {
}
chain filter_FWDO_public_post {
}
chain filter_FWDI_public {
jump filter_FWDI_public_pre
jump filter_FWDI_public_log
jump filter_FWDI_public_deny
jump filter_FWDI_public_allow
jump filter_FWDI_public_post
meta l4proto { icmp, ipv6-icmp } accept
}
chain filter_FWDI_public_pre {
}
chain filter_FWDI_public_log {
}
chain filter_FWDI_public_deny {
}
chain filter_FWDI_public_allow {
}
chain filter_FWDI_public_post {
}
chain mangle_PRE_public {
jump mangle_PRE_public_pre
jump mangle_PRE_public_log
jump mangle_PRE_public_deny
jump mangle_PRE_public_allow
jump mangle_PRE_public_post
}
chain mangle_PRE_public_pre {
}
chain mangle_PRE_public_log {
}
chain mangle_PRE_public_deny {
}
chain mangle_PRE_public_allow {
}
chain mangle_PRE_public_post {
}
chain filter_IN_policy_allow-host-ipv6 {
jump filter_IN_policy_allow-host-ipv6_pre
jump filter_IN_policy_allow-host-ipv6_log
jump filter_IN_policy_allow-host-ipv6_deny
jump filter_IN_policy_allow-host-ipv6_allow
jump filter_IN_policy_allow-host-ipv6_post
}
chain filter_IN_policy_allow-host-ipv6_pre {
}
chain filter_IN_policy_allow-host-ipv6_log {
}
chain filter_IN_policy_allow-host-ipv6_deny {
}
chain filter_IN_policy_allow-host-ipv6_allow {
icmpv6 type nd-neighbor-advert accept
icmpv6 type nd-neighbor-solicit accept
icmpv6 type nd-router-advert accept
icmpv6 type nd-redirect accept
}
chain filter_IN_policy_allow-host-ipv6_post {
}
chain mangle_PRE_policy_allow-host-ipv6 {
jump mangle_PRE_policy_allow-host-ipv6_pre
jump mangle_PRE_policy_allow-host-ipv6_log
jump mangle_PRE_policy_allow-host-ipv6_deny
jump mangle_PRE_policy_allow-host-ipv6_allow
jump mangle_PRE_policy_allow-host-ipv6_post
}
chain mangle_PRE_policy_allow-host-ipv6_pre {
}
chain mangle_PRE_policy_allow-host-ipv6_log {
}
chain mangle_PRE_policy_allow-host-ipv6_deny {
}
chain mangle_PRE_policy_allow-host-ipv6_allow {
}
chain mangle_PRE_policy_allow-host-ipv6_post {
}
chain filter_IN_libvirt {
jump filter_IN_libvirt_pre
jump filter_IN_libvirt_log
jump filter_IN_libvirt_deny
jump filter_IN_libvirt_allow
jump filter_IN_libvirt_post
accept
}
chain filter_IN_libvirt_pre {
}
chain filter_IN_libvirt_log {
}
chain filter_IN_libvirt_deny {
}
chain filter_IN_libvirt_allow {
udp dport 67 ct state { new, untracked } accept
udp dport 547 ct state { new, untracked } accept
tcp dport 53 ct state { new, untracked } accept
udp dport 53 ct state { new, untracked } accept
tcp dport 22 ct state { new, untracked } accept
udp dport 69 ct helper set "helper-tftp-udp"
udp dport 69 ct state { new, untracked } accept
meta l4proto icmp ct state { new, untracked } accept
meta l4proto ipv6-icmp ct state { new, untracked } accept
}
chain filter_IN_libvirt_post {
reject
}
chain filter_FWDO_libvirt {
jump filter_FWDO_libvirt_pre
jump filter_FWDO_libvirt_log
jump filter_FWDO_libvirt_deny
jump filter_FWDO_libvirt_allow
jump filter_FWDO_libvirt_post
accept
}
chain filter_FWDO_libvirt_pre {
}
chain filter_FWDO_libvirt_log {
}
chain filter_FWDO_libvirt_deny {
}
chain filter_FWDO_libvirt_allow {
}
chain filter_FWDO_libvirt_post {
}
chain filter_FWDI_libvirt {
jump filter_FWDI_libvirt_pre
jump filter_FWDI_libvirt_log
jump filter_FWDI_libvirt_deny
jump filter_FWDI_libvirt_allow
jump filter_FWDI_libvirt_post
accept
}
chain filter_FWDI_libvirt_pre {
}
chain filter_FWDI_libvirt_log {
}
chain filter_FWDI_libvirt_deny {
}
chain filter_FWDI_libvirt_allow {
}
chain filter_FWDI_libvirt_post {
}
chain mangle_PRE_libvirt {
jump mangle_PRE_libvirt_pre
jump mangle_PRE_libvirt_log
jump mangle_PRE_libvirt_deny
jump mangle_PRE_libvirt_allow
jump mangle_PRE_libvirt_post
}
chain mangle_PRE_libvirt_pre {
}
chain mangle_PRE_libvirt_log {
}
chain mangle_PRE_libvirt_deny {
}
chain mangle_PRE_libvirt_allow {
}
chain mangle_PRE_libvirt_post {
}
}
table ip firewalld {
chain nat_PREROUTING {
type nat hook prerouting priority dstnat + 10; policy accept;
jump nat_PREROUTING_POLICIES_pre
jump nat_PREROUTING_ZONES_SOURCE
jump nat_PREROUTING_ZONES
jump nat_PREROUTING_POLICIES_post
}
chain nat_PREROUTING_POLICIES_pre {
jump nat_PRE_policy_allow-host-ipv6
}
chain nat_PREROUTING_ZONES_SOURCE {
}
chain nat_PREROUTING_ZONES {
iifname "virbr0" goto nat_PRE_libvirt
iifname "eth0" goto nat_PRE_public
goto nat_PRE_public
}
chain nat_PREROUTING_POLICIES_post {
}
chain nat_POSTROUTING {
type nat hook postrouting priority srcnat + 10; policy accept;
jump nat_POSTROUTING_POLICIES_pre
jump nat_POSTROUTING_ZONES_SOURCE
jump nat_POSTROUTING_ZONES
jump nat_POSTROUTING_POLICIES_post
}
chain nat_POSTROUTING_POLICIES_pre {
}
chain nat_POSTROUTING_ZONES_SOURCE {
}
chain nat_POSTROUTING_ZONES {
oifname "virbr0" goto nat_POST_libvirt
oifname "eth0" goto nat_POST_public
goto nat_POST_public
}
chain nat_POSTROUTING_POLICIES_post {
}
chain nat_POST_public {
jump nat_POST_public_pre
jump nat_POST_public_log
jump nat_POST_public_deny
jump nat_POST_public_allow
jump nat_POST_public_post
}
chain nat_POST_public_pre {
}
chain nat_POST_public_log {
}
chain nat_POST_public_deny {
}
chain nat_POST_public_allow {
}
chain nat_POST_public_post {
}
chain nat_PRE_public {
jump nat_PRE_public_pre
jump nat_PRE_public_log
jump nat_PRE_public_deny
jump nat_PRE_public_allow
jump nat_PRE_public_post
}
chain nat_PRE_public_pre {
}
chain nat_PRE_public_log {
}
chain nat_PRE_public_deny {
}
chain nat_PRE_public_allow {
}
chain nat_PRE_public_post {
}
chain nat_PRE_policy_allow-host-ipv6 {
jump nat_PRE_policy_allow-host-ipv6_pre
jump nat_PRE_policy_allow-host-ipv6_log
jump nat_PRE_policy_allow-host-ipv6_deny
jump nat_PRE_policy_allow-host-ipv6_allow
jump nat_PRE_policy_allow-host-ipv6_post
}
chain nat_PRE_policy_allow-host-ipv6_pre {
}
chain nat_PRE_policy_allow-host-ipv6_log {
}
chain nat_PRE_policy_allow-host-ipv6_deny {
}
chain nat_PRE_policy_allow-host-ipv6_allow {
}
chain nat_PRE_policy_allow-host-ipv6_post {
}
chain nat_POST_libvirt {
jump nat_POST_libvirt_pre
jump nat_POST_libvirt_log
jump nat_POST_libvirt_deny
jump nat_POST_libvirt_allow
jump nat_POST_libvirt_post
}
chain nat_POST_libvirt_pre {
}
chain nat_POST_libvirt_log {
}
chain nat_POST_libvirt_deny {
}
chain nat_POST_libvirt_allow {
}
chain nat_POST_libvirt_post {
}
chain nat_PRE_libvirt {
jump nat_PRE_libvirt_pre
jump nat_PRE_libvirt_log
jump nat_PRE_libvirt_deny
jump nat_PRE_libvirt_allow
jump nat_PRE_libvirt_post
}
chain nat_PRE_libvirt_pre {
}
chain nat_PRE_libvirt_log {
}
chain nat_PRE_libvirt_deny {
}
chain nat_PRE_libvirt_allow {
}
chain nat_PRE_libvirt_post {
}
}
table ip6 firewalld {
chain nat_PREROUTING {
type nat hook prerouting priority dstnat + 10; policy accept;
jump nat_PREROUTING_POLICIES_pre
jump nat_PREROUTING_ZONES_SOURCE
jump nat_PREROUTING_ZONES
jump nat_PREROUTING_POLICIES_post
}
chain nat_PREROUTING_POLICIES_pre {
jump nat_PRE_policy_allow-host-ipv6
}
chain nat_PREROUTING_ZONES_SOURCE {
}
chain nat_PREROUTING_ZONES {
iifname "virbr0" goto nat_PRE_libvirt
iifname "eth0" goto nat_PRE_public
goto nat_PRE_public
}
chain nat_PREROUTING_POLICIES_post {
}
chain nat_POSTROUTING {
type nat hook postrouting priority srcnat + 10; policy accept;
jump nat_POSTROUTING_POLICIES_pre
jump nat_POSTROUTING_ZONES_SOURCE
jump nat_POSTROUTING_ZONES
jump nat_POSTROUTING_POLICIES_post
}
chain nat_POSTROUTING_POLICIES_pre {
}
chain nat_POSTROUTING_ZONES_SOURCE {
}
chain nat_POSTROUTING_ZONES {
oifname "virbr0" goto nat_POST_libvirt
oifname "eth0" goto nat_POST_public
goto nat_POST_public
}
chain nat_POSTROUTING_POLICIES_post {
}
chain nat_POST_public {
jump nat_POST_public_pre
jump nat_POST_public_log
jump nat_POST_public_deny
jump nat_POST_public_allow
jump nat_POST_public_post
}
chain nat_POST_public_pre {
}
chain nat_POST_public_log {
}
chain nat_POST_public_deny {
}
chain nat_POST_public_allow {
}
chain nat_POST_public_post {
}
chain nat_PRE_public {
jump nat_PRE_public_pre
jump nat_PRE_public_log
jump nat_PRE_public_deny
jump nat_PRE_public_allow
jump nat_PRE_public_post
}
chain nat_PRE_public_pre {
}
chain nat_PRE_public_log {
}
chain nat_PRE_public_deny {
}
chain nat_PRE_public_allow {
}
chain nat_PRE_public_post {
}
chain nat_PRE_policy_allow-host-ipv6 {
jump nat_PRE_policy_allow-host-ipv6_pre
jump nat_PRE_policy_allow-host-ipv6_log
jump nat_PRE_policy_allow-host-ipv6_deny
jump nat_PRE_policy_allow-host-ipv6_allow
jump nat_PRE_policy_allow-host-ipv6_post
}
chain nat_PRE_policy_allow-host-ipv6_pre {
}
chain nat_PRE_policy_allow-host-ipv6_log {
}
chain nat_PRE_policy_allow-host-ipv6_deny {
}
chain nat_PRE_policy_allow-host-ipv6_allow {
}
chain nat_PRE_policy_allow-host-ipv6_post {
}
chain nat_POST_libvirt {
jump nat_POST_libvirt_pre
jump nat_POST_libvirt_log
jump nat_POST_libvirt_deny
jump nat_POST_libvirt_allow
jump nat_POST_libvirt_post
}
chain nat_POST_libvirt_pre {
}
chain nat_POST_libvirt_log {
}
chain nat_POST_libvirt_deny {
}
chain nat_POST_libvirt_allow {
}
chain nat_POST_libvirt_post {
}
chain nat_PRE_libvirt {
jump nat_PRE_libvirt_pre
jump nat_PRE_libvirt_log
jump nat_PRE_libvirt_deny
jump nat_PRE_libvirt_allow
jump nat_PRE_libvirt_post
}
chain nat_PRE_libvirt_pre {
}
chain nat_PRE_libvirt_log {
}
chain nat_PRE_libvirt_deny {
}
chain nat_PRE_libvirt_allow {
}
chain nat_PRE_libvirt_post {
}
}
[root@kvmhost8 ~]# firewall-cmd --state
running
[root@kvmhost8 ~]# firewall-cmd --get-default-zone
public
[root@kvmhost8 ~]# firewall-cmd --get-active-zones
libvirt
interfaces: virbr0
public
interfaces: eth0
[root@kvmhost8 ~]# firewall-cmd --get-zones
block dmz drop external home internal libvirt nm-shared public trusted work
[root@kvmhost8 ~]# firewall-cmd --info-zone=public
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@kvmhost8 ~]# firewall-cmd --info-zone=libvirt
libvirt (active)
target: ACCEPT
icmp-block-inversion: no
interfaces: virbr0
sources:
services: dhcp dhcpv6 dns ssh tftp
ports:
protocols: icmp ipv6-icmp
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule priority="32767" reject